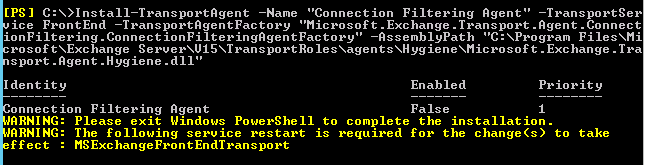
Windows Explorer and many Windows applications including PowerShell are limited to 255 characters max file path. Whilst this limitation is in place at an application level, the NTFS file system does not support this limit. In fact file paths can be created remotely over the SMB protocol to exceed this limit which is how most file servers get stuck with folder paths administrators can no longer maintain using the native Windows Explorer application.
When attempting to delete folders using Windows Explorer the following errors may be experienced:
The source file name(s) are larger than is supported by the file system. Try moving to a location which has a shorter path name, or renaming to shorter name(s) before attempting this operation.
I am going to show you a way to remove excessively long file paths without using third party tools such as Long Path Tool which come at a price or booting into different operating systems such as Linux to remove the unwanted file paths.
One Microsoft application which is not limited to the 255 character limit is robocopy.exe. I know this as I often move large volumes of data with Robocopy between server infrastructure and have never been hit with a file path limitation. As a result, this is the tool I chose to remove the data.
If you use robocopy with the /MIR switch, it will make the destination folder exactly the same as the source folder. So if the source folder is empty, it will delete all data in the destination empty and in result deleting the content.
I have a path here with 3 users which have folder structures which exceed 255 characters. Windows Explorer failed to remove these folders.
I created an empty folder on C:\ called test then used the mirror switch to copy the test folder to the HomeDrives folder.
robocopy /MIR c:\test E:\UserData\HomeDrives
After running the command all my user folders under E:\UserData\HomeDrives were deleted.
This is a handy trick for dealing with folders on file servers which have excessive amounts of long folder structures which exceed the 255 character limit.
Hope this has been helpful, feel free to leave me a comment below.
When attempting to delete folders using Windows Explorer the following errors may be experienced:
The source file name(s) are larger than is supported by the file system. Try moving to a location which has a shorter path name, or renaming to shorter name(s) before attempting this operation.
An unexpected error is keeping you from deleting the folder. If you continue to receive this error, you can use the error code to search for help with this problem.
Error: 0x80004005: Unspecified error
Even new applications from Microsoft such as PowerShell do not support file paths longer then 255 characters despite this being supported by NTFS.
Remove-Item: The specified path, file name, or both are too long. The fully qualified file name must be less than 260 characters, and the directory name must be less then 248 characters.
I am going to show you a way to remove excessively long file paths without using third party tools such as Long Path Tool which come at a price or booting into different operating systems such as Linux to remove the unwanted file paths.
One Microsoft application which is not limited to the 255 character limit is robocopy.exe. I know this as I often move large volumes of data with Robocopy between server infrastructure and have never been hit with a file path limitation. As a result, this is the tool I chose to remove the data.
If you use robocopy with the /MIR switch, it will make the destination folder exactly the same as the source folder. So if the source folder is empty, it will delete all data in the destination empty and in result deleting the content.
I have a path here with 3 users which have folder structures which exceed 255 characters. Windows Explorer failed to remove these folders.
I created an empty folder on C:\ called test then used the mirror switch to copy the test folder to the HomeDrives folder.
robocopy /MIR c:\test E:\UserData\HomeDrives
After running the command all my user folders under E:\UserData\HomeDrives were deleted.
This is a handy trick for dealing with folders on file servers which have excessive amounts of long folder structures which exceed the 255 character limit.
Hope this has been helpful, feel free to leave me a comment below.