Windows Troubleshooting Platform or WTP for short is a new tool included with Windows 7 to allow users to automatically resolve problems with their PC reducing calls to the help desk. To quickly get up to speed with WTP please watch this
demo video by Microsoft.
To get to WTP in control panel go to:
System and Security --> Action Center --> Troubleshooting
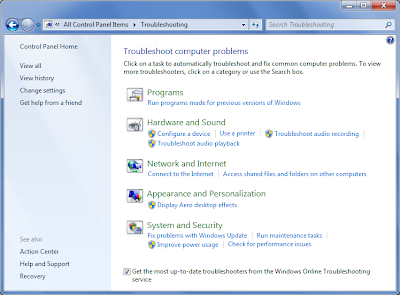
Each catagory in the trouble shooting panel launches different trouble shooting packs. Windows 7 can also automatically download additional trouble shooting packs as released by Microsoft if the tickbox in Trouble shooting is ticked.
Below are the three core components that make WTP work:
Troubleshooting WizardThe UI component communicates with the troubleshooting engine to walk the user through the steps defined in a troubleshooting pack.
Troubleshooting PacksThese packs each consist of an XML manifest file that specifies the root causes of a condition and Windows PowerShell scripts that detect the condition, resolve the underlying issue, and verify that the issue has been resolved.
WTP is also very extendable, Microsoft released a framework so IT Administrators can develope their own troubleshooting packs for issues that are unique to their environment.
Troubleshooting EngineThis component launches a Windows PowerShell runtime that executes a troubleshooting pack. It also exposes a set of interfaces for controlling the execution of the pack.
Advanced WTPI'm going to spend a little more time on WTP as I think its a really powerful feature and can service desks life so easy. For example you have software phones and users keep accidently disabling their sound, or muting their microphone. WTP can just allow users to click a fix button and everything magically starts working again. All the information you could ever need about WTP can be found on
WTP TechNet Home Page. As you can see from the picture below this technet site it goes through the powershell cmdlets around WTP as well as loads of information and example code for making your own troubleshooting packs.
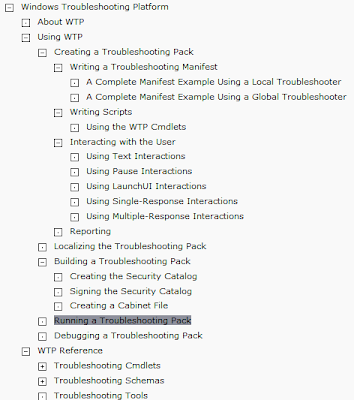 WTP In Powershell
WTP In PowershellLastly we are going to go through some of the handy powershell commands in Windows 7.
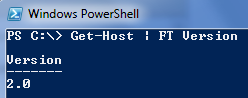
I would like to point out quickly that Windows 7 is the first version of windows to come with powershell built into the operating system. All previous versions like vista, windows 2008 and XP did not come with powershell and you had to either add powershell in as a feature or download it from the internet. Also windows 7 is currently running powershell version 2.0. Version 2.0 is not available for any other operating system apart from 2008 R2 at this stage, but it should be released for the other versions of windows soon. To show you this I will run Get-Host FT Version which wills how you the version of powershell we are currently running:
Before we can use the CmdLets for WTP we need to import the module into the powershell session. This goes with all windows applications that support powershell, to be able to use the cmdlets for that particular application the module needs to be loaded. To list all modules available on a system run:
get-module -listavailable
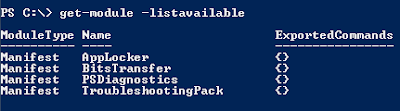
On a platform such as server 2008 there is loads more modules because its a server platform. Theres modules for pretty much every thing you want to control from NLB to cluster services and even other packages you purchase such as exchange 2007/2010, SCOM and SCCM.
It is possible to import all modules by running:
get-module -ListAvailable import-module
However this means you have all the cmdlets at your disposal and many of these you will not need for the operation your performing and it makes everything very confusing! Just import the TroubleShooting Pack module for WTP by running:
Import-Module TroubleshootingPack
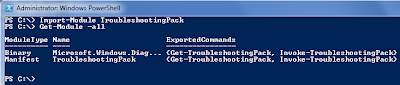
Get-Module -all shows us the module is active.
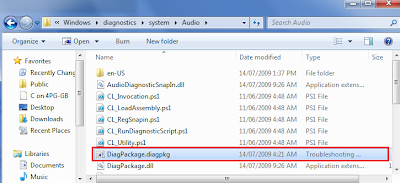
The TroubleshootingPack's that come with windows are located under:
C:\Windows\diagnostics
However you can also run troubleshooting packs of network drives handy for when you wish to publish additional trouble shooting packs to workstations you do not need to copy the files to each machine. If you wish to view a troubleshooting pack you would do this with the Get-TroubleshootingPack cmdlet:
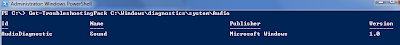
This is the pack that fixes audio problems related to windows 7. You can also run the troubleshooting packs from powershell:
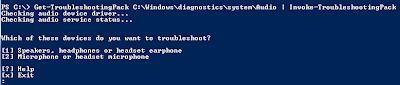
While we were talking about powershell modules i'd like to quickly show you how to get all commands for a module. You simply type:
Get-Command -Module "modulename"
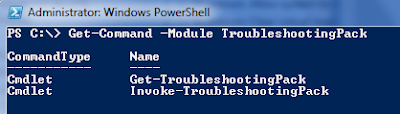
As you can see there are only two powershell cmdlets for WTP making it real easy for us to remember :).
Troubleshooting Pack DeploymentIf you have downloaded or created your own troubleshooting pack you will need to deploy it. Troubleshooting packs contain .diagcab files that are created using the Makecab.exe or Cabarc.exe tools located in the %Windir%\System32 folder. They also contain security catalogs created using tools such as makecat.exe from the windows SDK.
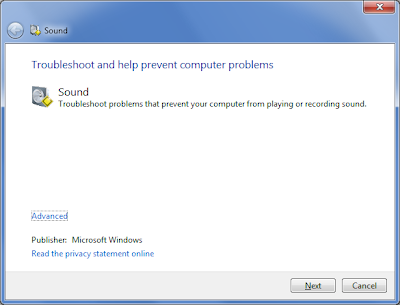
These .diagcab files can be distributed by using Group Policy Preferences, Microsoft System Center Configuration Manager (during or after deployment), or software distribution tools. You can even post the .diagcab files to a internal web site and users can launch them directly of the web server. The user will get presented with a nice GUI the same as going through control panel. For example if I manually double click on the sound troubleshooting .diagcab file I will get presented with a sound trouble shooting wizard: