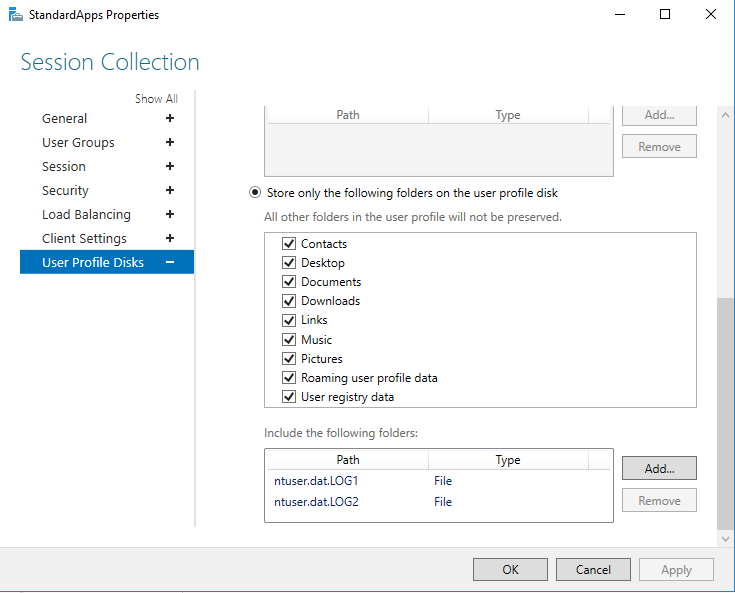
In this post I will be going through some of the new features that are included in Windows Server 2008 terminal services. It frustrates me as many people do not know how powerful 2008 terminal services are now compared to server 2003. When most people (including administrators) think of "Terminal Services" they think of the functionality that of which was provided by Server 2003 which I can say was very limited! It also frustrates me that many companies implement Citrix as their terminal server solution blowing money away that is no longer needed to be spent. There are business cases for when you would need to use Citrix over 2008 Terminal Services however for many companies using Citrix, they do not require it - they were simply sold it as the sales guy did not know better.
Please note that these features listed below are those of which came with Windows Server 2008 RTM, not Windows Server 2008 R2. Microsoft actually changed the name in Server 2008 R2 from Terminal Services to RDS (Remote Desktop Services). But again we will not be going into the R2 stuff, only standard Terminal Services features that came with Server 2008.
Terminal Services RemoteApp
Previously in server 2003 you could only present a entire desktop to a terminal server user. Now with server 2008 you can present just applications to workstations. If the program uses a notification area icon, that icon appears in the client’s notification area. Pop-up windows are redirected to the local desktop and local drives and printers are redirected and made available within the remote program. Users may even be unaware that the remote program is any different than other local applications running side-by-side with the remote program on their desktop because similar functionality, such as cut and paste, are available. Also if a user opened a .doc file on their local machine in their my documents folder, and they have Microsoft Word presented to them by a Microsoft Remote App server, file extensions carry accross so the document file will actually open up in the terminal session - the user will not have a clue what goes on in the back end.
RemoteApp programs are programs that are accessed remotely through Terminal Services and appear as if they are running on the end user's local computer. Users can run programs from a terminal server and have the same experience as if the programs were running on their local computer, including resizable windows, drag-and-drop support between multiple monitors, and notification icons in the notification area.
Here is an example of OneNote running as a RemoteApp mixed with real physical Apps on a vista PC. Click to make it bigger.

Users can run RemoteApp programs side by side with their local programs. They can minimize, maximize, and resize the program window as well as cut and paste, and easily start multiple programs at the same time. If a user is running more than one RemoteApp program on the same terminal server, the RemoteApp programs will share the same Terminal Services session.
There are many ways of deploying remote apps to workstations however there is only one way I would recommend and that is to package the application as an msi using the remote apps MMC console on the server, then using group policy to push it out to the workstations. These MSI's are very small, all they do is add the icons (or shortcuts if you will) and create the file associations on the users workstation.
Users can run RemoteApp programs in a number of ways:
• Double-click a Remote Desktop Protocol (.rdp) file that has been created and distributed by their administrator.
• Double-click a program icon on their desktop or Start menu that has been created and distributed by their administrator with a Windows Installer (.msi) package.
• Double-click a file whose extension is associated with a RemoteApp program. (This can be configured by their administrator with a Windows Installer package.)
• Access a link to the RemoteApp program on a Web site by using Terminal Services Web Access (TS Web Access).
Terminal Services Web Access
Terminal Services Web Access (TS Web Access) is a service within Terminal Services that lets you make TS RemoteApp programs, and a link to the terminal server desktop, available to users from a Web browser. Additionally, TS Web Access enables users to launch a connection from a Web browser to the remote desktop of any server or client computer where they have the appropriate access.
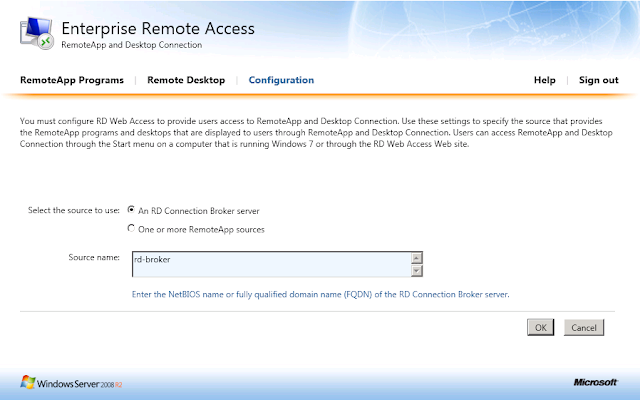
Here is an example of what the TS Web Access portal looks like:

TS Web Access acts as the access or launch mechanism in conjunction with TS Gateway, to enable you to easily deploy RemoteApp programs over the internet in conjunction with TS Web Access. A user can visit a Web site, view a list of RemoteApp programs, and then simply click on a program icon to start the program. The RemoteApp programs are seamless, meaning that they appear like a local program. Users can minimize, maximize, and resize the program window, and can easily start multiple programs at the same time. For an administrator, TS Web Access is easy to configure and to deploy.
TS Web Access is very user friendly compared to other vendors that provide the same services. This is because users do not have to download a separate ActiveX control to access TS Web Access. Instead, RDC 6.1 includes the required ActiveX control. (The RDC 6.1 client supports Remote Desktop Protocol 6.1.) RDC 6.1 is included in Vista SP1 and Windows XP SP3 and combines both the traditional RDC and the ActiveX control. Citrix users will still need to download and install the Active X control to connect in which generates majority of your help desk calls. Also having done a bit of desktop support in my past years, I remember when there were citrix updates for the citrix terminal servers, and users still had the old ActiveX controls on their workstations. These didn't automatically update, I had to walk around to everyone's workstation, uninstall the old ActiveX control so it would automatically download the new one.
The TS Web Access portal is just as customizable as Citrix. You can add custom company banners, change colours and feel of the page, deploy as part of a customized webpage using ActiveX and ASP (Terminal Services client is fully scripable) - for more information visit
http://msdn2.microsoft.com/en-us/library/aa383022(VS.85).aspx. You can integrate it in as part of a sharepoint service site, or you could be lazy like me and just deploy it as the default out-of-box solution. I'm not one for customizing and pretty colours.
As an administrator, you can use IIS application settings to configure whether the Remote Desktop tab is available to users. Additionally, you can configure settings such as the TS Gateway server to use, the TS Gateway authentication method, and the default device and resource redirection options.
Terminal Services Gateway
Terminal Services Gateway (TS Gateway) is a role service that allows authorized remote users to connect to terminal services based resources on an internal corporate or private network, from Internet-connected devices. The network resources can be terminal servers, terminal servers running RemoteApp programs, or computers with Remote Desktop enabled.
TS Gateway uses Remote Desktop Protocol (RDP) encapsulated in RPC over HTTPS to establish a secure, encrypted connection between remote users on the Internet and the internal network resources on which their productivity applications run.

If your organization makes Terminal Services–based applications and computers that run Remote Desktop available to users from outside your network perimeter, TS Gateway can simplify network administration and reduce your exposure to security risks. TS Gateway can also make it easier for users because they do not have to configure VPN connections and can access TS Gateway servers from sites that can otherwise block outbound RDP or VPN connections. Note if your users need more then RDP 3389 externally then I would still recommend VPN.
TS Gateway provides a secure yet flexible RDP connection allowing users access to anything to which their RDP host has access, rather than allowing remote users direct network connectivity to all internal network resources; helping protect the internal resources.
The TS Gateway Manager snap-in console enables you to configure authorization policies to define conditions that must be met for remote users to connect to internal network resources. For example, you can specify:
• Who can connect to network resources (in other words, the user groups who can connect).
• What network resources (computer groups) users can connect to.
• Whether client computers must be members of Active Directory® security groups.
• Whether device and disk redirection is allowed.
• Whether clients need to use smart card authentication or password authentication, or whether they can use either method.
TS Gateway also has full built in support for NAP (Network Access Protection) to ensure all remote clients accessing your network are virus free, up to date in patch level and have an active firewall running. The NAP Client is built into the Microsoft Security Center which is on all windows releases from Windows XP SP3 and higher.
You can use TS Gateway server with Microsoft Internet Security and Acceleration (ISA) Server to enhance security. In this scenario, you can host TS Gateway servers in a private network rather than a perimeter network and screened subnet), and host ISA Server in the perimeter network. The SSL connection between the Terminal Services client and ISA Server can be terminated at the ISA Server, which is Internet-facing.
The TS Gateway Manager snap-in console provides tools to help you monitor TS Gateway connection status, health, and events. By using TS Gateway Manager, you can specify events (such as unsuccessful connection attempts to the TS Gateway server) that you want to monitor for auditing purposes. There is also full SCOM integration for this so you can monitor your terminal services health all from OpsMgr 2007.
TS Gateway provides several new features to simplify administration and enhance security.
Monitoring Capabilities: You can use TS Gateway Manager to view information about active connections from Terminal Services clients to internal corporate network resources through TS Gateway. This information includes the connection ID, the domain and user ID of the user logged on to the client, full name of the user logged on to the client, date and time when the connection was initiated, length of time the connection was active, length of time that the connection is idle- if applicable, name of the internal network computer to which the client is connected, IP address of the client.
Group Policy Settings for TS Gateway: You can use Group Policy and Active Directory Domain Services to centralize and simplify the administration of TS Gateway policy settings. You use the Local Group Policy Editor to configure local policy settings, which are contained within Group Policy Objects (GPOs). You use the Group Policy Management Console (GPMC) to link GPOs to sites, domains, or organizational units (OUs) in Active Directory Domain Services. Group Policy settings for Terminal Services client connections through TS Gateway can be applied in one of two ways. These policy settings can either be suggested (that is, they can be enabled, but not enforced) or they can be enabled and enforced. Suggesting a policy setting allows users on the client to enter alternate TS Gateway connection settings. Enforcing a policy setting prevents a user from changing the TS Gateway connection setting, even if they select the Use these TS Gateway server settings option on the client.
TS CAPs: Terminal Services connection authorization policies (TS CAPs) allow you to specify user groups, and optionally client computer groups, that can access a TS Gateway server. You can create a TS CAP by using TS Gateway Manager. TS CAPs simplify administration and enhance security by providing a greater level of control over access to computers on your internal network. TS CAPs also allow you to specify who can connect to a TS Gateway server. You can specify a user group that exists on the local TS Gateway server or in Active Directory Domain Services. You can also specify other conditions that users must meet to access a TS Gateway server. You can list specific conditions in each TS CAP. For example, you might require a user to use a smart card to connect through TS Gateway. Users are granted access to a TS Gateway server if they meet the conditions specified in the TS CAP.
TS RAPs: Terminal Services remote authorization policies (TS RAPs) allow you to specify the internal corporate network resources that remote users can connect to through a TS Gateway server. When you create a TS RAP, you can create a computer group (a list of computers on the internal network to which you want the remote users to connect) and associate it with the TS RAP. Remote users connecting to an internal network through a TS Gateway server are granted access to computers on the network if they meet the conditions specified in at least one TS CAP and one TS RAP. Together, TS CAPs and TS RAPs provide two different levels of authorization to provide you with the ability to configure a more specific level of access control to computers on an internal network.
Terminal Services Session Broker
Terminal Services Session Broker (TS Session Broker) is a role service in Windows Server 2008 that allows a user to reconnect to an existing session in a load-balanced terminal server farm. TS Session Broker stores session state information that includes session IDs and their associated user names, and the name of the server where each session resides. I had someone from Citrix come out and give a presentation trying to tell us it worked the same as NLB (which was used in server 2003) - shows how out of date peoples knowledge in this area is.
The new TS Session Broker Load Balancing feature enables you to evenly distribute the session load between servers in a load-balanced terminal server farm. With TS Session Broker Load Balancing, new user sessions are redirected to the terminal server with the fewest sessions.
TS Session Broker is a two phased load-balancing mechanism. In the first phase, initial connections are distributed by a preliminary load-balancing mechanism, such as DNS round robin. After a user authenticates, the terminal server that accepted the initial connection queries the TS Session Broker server to determine where to redirect the user.
In the second phase, the terminal server where the initial connection was made redirects the user to the terminal server that was specified by TS Session Broker. The redirection behavior is as follows:
• A user with an existing session will connect to the server where their session exists.
• A user without an existing session will connect to the terminal server that has the fewest sessions
TS Session Broker Load Balancing sets a (total combined) limit of 16 for the maximum number of pending logon requests to a particular terminal server. This helps to prevent the scenario where a single server is overwhelmed by new logon requests; for example, if you add a new server to the farm, or if you enable user logons on a server where they were previously denied.
The TS Session Broker Load Balancing feature also enables you to assign a relative weight value to each server. By assigning a server weight value, you can help to distribute the load between more powerful and less powerful servers in the farm.
A User logon mode setting is provided that enables you to prevent new users from logging on to a terminal server that is scheduled to be taken down for maintenance. This mechanism provides for the ability to take a server offline without disrupting the user experience. If new logons are denied on a terminal server in the farm, TS Session Broker will allow users with existing sessions to reconnect, but will redirect new users to terminal servers that are configured to allow new logons.
You can still use load balancing techniques such as NLB or Round-Robin DNS to load balance 2008 terminal servers buy why would you when you have TS Session Broker.
Terminal Services Easy Print
Terminal Services Easy Print (TS Easy Print) is a feature in Windows Server 2008 that enables users to reliably print from a TS RemoteApp program or from a TS remote desktop session to the correct printer on their client computer. Microsoft Easy Print is better then the Citrix universal print driver as the universal print driver supports most printers however easy print supports all printers provided there is a driver on the client PC. Terminal Services Easy Print leverages the client-side print driver (no server side driver needed) to enable fast and reliable printing to a local or network-attached printer. End users can more productively work from remote locations. It also enables users to have a much more consistent printing experience between local and remote sessions.
The Redirect only the default client printer policy setting allows you to specify whether the default client printer is the only printer that is redirected in Terminal Services sessions. This helps to limit the number of printers that the spooler must enumerate, therefore improving terminal server scalability.
To use the TS Easy Print driver, clients must be running both of the following:
• Remote Desktop Connection (RDC) 6.1
• Microsoft .NET Framework 3.0 Service Pack 1 (SP1)
Also new in Windows Server 2008 Terminal Services is the Use Terminal Services Easy Print printer driver first Group Policy for Terminal Services printing located in the following node of the Local Group Policy Editor: Computer Configuration\Administrative Templates\Windows Components\Terminal Services\Terminal Server\Printer Redirection.
Terminal Services Licensing
Yes - still the same old stuff here. Distributes licences to each of your terminal servers on your network. Can distribute licences to multiple farms. You normally want to put this on a server as an additional role as it does not use hardly any CPU usage or memory usage.
Terminal Services and Windows System Resource Manager
Windows System Resource Manager (WSRM), allows you to control how CPU and memory resources are dynamically allocated to applications, services, and processes. Managing resources in this way improves system performance and reduces the chance that applications, services, or processes will interfere with the rest of the system. It also creates a more consistent and predictable experience for users of applications and services running on the computer.
You can use WSRM to resource allocation of the following things:
• TS Sessions on a terminal server
• Users on a server (users are seperate because remember it is possible to have 1 user with multiple sessions open in effect eating up all the resources on the terminal server). You can manage users by security group!
• Administering resource usage of multiple Microsoft SQL Server® instances sharing a server.
• Administering resource usage of IIS 6.0 application pools on a server, such as when one server hosts multiple Web sites.
• Reports on memory usage and CPU time to support service level agreement (SLA) metrics.
What you can do with WSRM is ensure that no applications eat up all processing power on a terminal server, or that 1 user or TS session does not hog all available processing power to the server. Windows System Resource Manager is a feature that is built into all 2008 servers and should be used to ensure no server has a memory leak or constant processor loop but it is particulary handy on terminal servers. I'd always lock it down to either TS Session or TS Users and you can do this to all terminal servers in your farm by simply using a group policy.
With WSRM you can ensure that everyone has an equal share to a terminal servers resources!
Other New Features
Large Display Support - Custom display resolution provides support for large display and additional display resolution ratios (up to 4096x2048). Additionally, only 4:3 display resolution ratios were supported, now can create custom ratios like 16:9 or 16:10. Finally, full 32-bit color depth is now enabled and with the new compression engine 32-bit color will typically consume less bandwidth than 24-bit color. You can set a custom display resolution in an .rdp file or from a command prompt.
Multiple Monitor Support - Monitor spanning allows you to display your remote desktop session across multiple monitors (only support for horizontal spanning); you can enable it in an .rdp file or from a command prompt by including the /span switch.
Vista Experiance - You can enable Vista Experiance on your 2008 server to give your users the full Areo desktop experiance - ooooo fancy!
RDP Protocol and Advanced Compression - Terminal Services delivers applications and data via the Remote Desktop Protocol (RDP), an optimized transport mechanism low bandwidth. Traditional client server applications that slow end-user productivity over a slow network connection, receive a performance boost when delivered via Terminal Services to remote users. This compression is not as great as ICA but it is getting there.
PnP Device Redirection Framework - The PnP Device Redirection Framework enables driver vendors to create device drivers to ensure their hardware can be utilized remotely over RDP. Microsoft includes “out-of-the-box” support for MTP Devices (Cameras and MP3 players that have a Windows mode) and Windows Embedded Point of Service Devices (WePOS).
Advanced Clipboard Redirection - The clipboard had been improved with Windows Server 2008 Terminal Services to enable stream support. This improves the performance of redirected drives, enable support for more types of data to be exchange via cut and paste e.g graphics, files, office data etc. I think this is fantastic I use it all the time - copying and pasting images in and out of RDP sessions.
Wildcard SSL Certificate Support - SSL certificates are used in TS Gateway, TS Web Access, RDP Signing and TLS Authentication. Obtaining multiple SSL certificates for all of these purposes can, for some customers, be both costly and a management challenge. TS supports Wildcard SSL certificates for all these purposes, Wildcard certificates provides a single certificate than can be used on multiple machines.
RDP Signing - RDP signing allows signing of RDP files and connections launched from TS Web Access. This helps the user be sure that they are not using malicious RDP files to potentially connect to hostile terminal servers. It is also possible, using group policy, to specify that a user can only launched signed files. This allows administrators to ensure that users only connect to know resources.
Clint's Wrap Up
These features listed above are those of what were released in the initial 2008 RTM release. With R2 and RDS (Remote Desktop Services) the Microsoft terminal technology has taken another huge leap forward - when I get time I will write another blog post of what new features have been introduced into R2 terminal services.
One thing I will admit though is Citrix is still a better solution - one of the key factors behind their success is the ICA protocol. It's bandiwidth utilization is amazing. However one thing I would like to achieve is majority of the selling points Citrix are still using (even the citrix engineers) are features that are natively supported in Windows Server - so why would you go pay for them?
Companys that have huge branch offices with an extremely slow link such as a remote mine site would definately benefit from Citrix because they can take advantage of ICA enhancers such as their WAN Scaler.
However I think for majority of businesses they would be wasting money for software that is not needed.
I would love feedback - feel free to contact me on clint@kbomb.com.au